Are you also a victims of this CTB-Locker(Critoni) virus? Here in this post, you can get more information about this nasty virus and hope the guide can help you remove CTB-Locker(Critoni) from your computer.
Brief Introduction about CTB-Locker(Critoni)
Similar to CryptoLocker, CTB-Locker(Critoni) is another encryption ransomware virus which will get into the computer to encrypt all your files. It will also give the instruction to pay for the ransom to get the private decryption key to recover the files. It will send a timer to threaten you to pay the ransom as soon as possible. If you don'y pay the ransom in time,the key will be deleted.
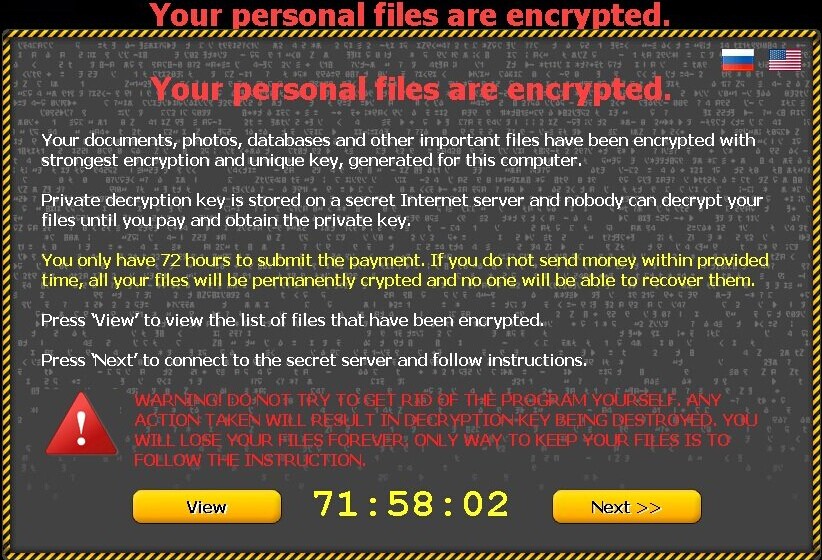
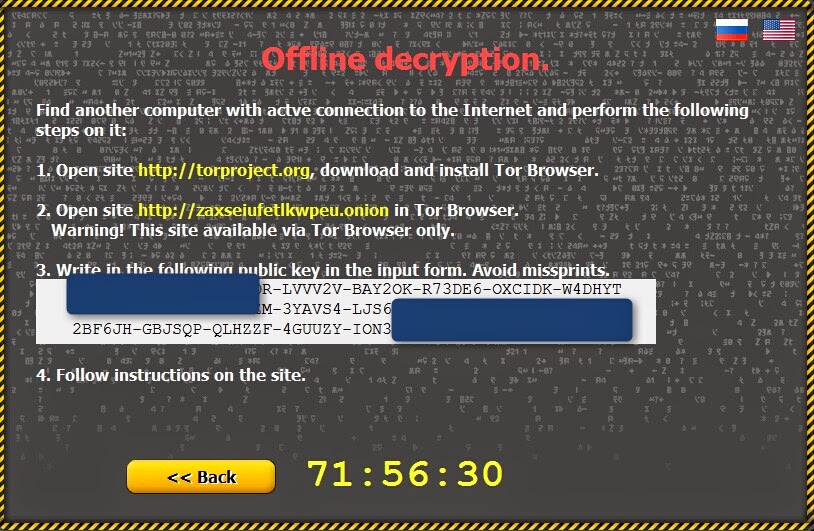
It will give the instruction to guide you to pay for the ransom. It asks you to follow the webpage of to download and install tor-browser from the listed website in the below screenshot. This ransomware uses unique bitcoin payment addresses for each victim instead of hard coded links. The cyber criminals will also use their own TOR gateways to stay hidden from the authorities.
%2B2.jpg)
You should not follow its steps to pay the ransom, there is no guarantee. It is important to regularly create back ups in your daily work. In order to stop CTB-Locker(Critoni) virus keep encrypting your new files and data, you should remove this virus from your computer immediately. You can follow the removal guide below.
Similar to CryptoLocker, CTB-Locker(Critoni) is another encryption ransomware virus which will get into the computer to encrypt all your files. It will also give the instruction to pay for the ransom to get the private decryption key to recover the files. It will send a timer to threaten you to pay the ransom as soon as possible. If you don'y pay the ransom in time,the key will be deleted.

It will give the instruction to guide you to pay for the ransom. It asks you to follow the webpage of to download and install tor-browser from the listed website in the below screenshot. This ransomware uses unique bitcoin payment addresses for each victim instead of hard coded links. The cyber criminals will also use their own TOR gateways to stay hidden from the authorities.
%2B2.jpg)
You should not follow its steps to pay the ransom, there is no guarantee. It is important to regularly create back ups in your daily work. In order to stop CTB-Locker(Critoni) virus keep encrypting your new files and data, you should remove this virus from your computer immediately. You can follow the removal guide below.

It will give the instruction to guide you to pay for the ransom. It asks you to follow the webpage of to download and install tor-browser from the listed website in the below screenshot. This ransomware uses unique bitcoin payment addresses for each victim instead of hard coded links. The cyber criminals will also use their own TOR gateways to stay hidden from the authorities.
%2B2.jpg)
You should not follow its steps to pay the ransom, there is no guarantee. It is important to regularly create back ups in your daily work. In order to stop CTB-Locker(Critoni) virus keep encrypting your new files and data, you should remove this virus from your computer immediately. You can follow the removal guide below.
CTB-Locker(Critoni) Removal Guide
Guide 1: To manually delete all its related items like the steps showed below
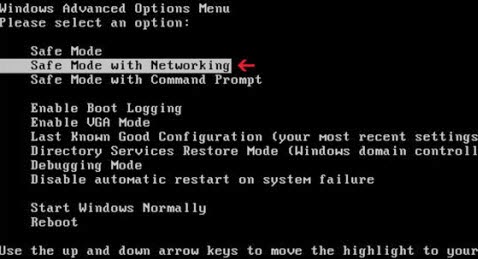
Step 1: Restart computer in safe mode.
Keep pressing F8 key before Windows interface launches. When Windows Advanced Options menu turns up, select Safe Mode with Networking and tap Enter key.
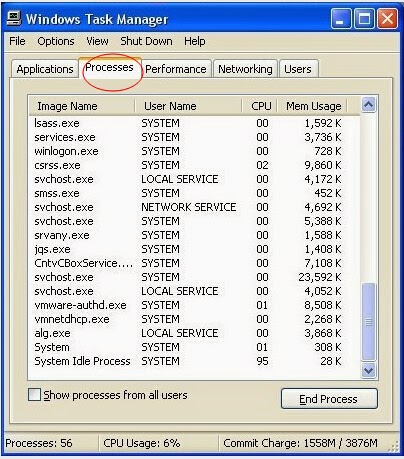
Step 2: End all running process in Task Manager

Press Ctrl+Alt+Del together to open Task Manager -> click on processes and tick Processes from all users box -> click on End Process to end all processes
Step 3: Delete the rogue program from Uninstall a program in Control Panel
Open Start menu and choose Control Panel -> select Uninstall a program -> choose the program and right click the Uninstall button on your right to delete it
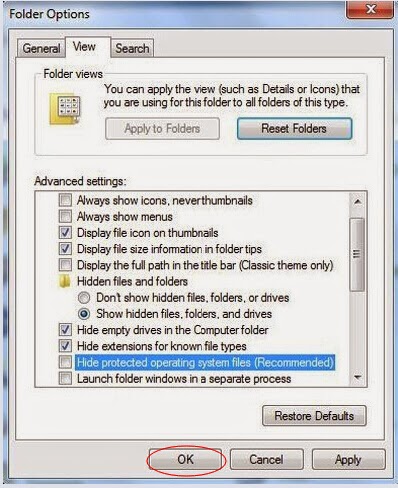
Step 4: Open Control Panel from Start menu and search for Folder Options.
When Folder Options window opens, click on its View tab, tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then press OK.
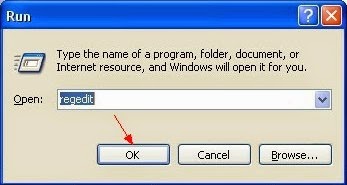
Step 5: Remove all entries below in Registry Editor:
Press Windows+R to launch Run…-> type Regedit into Open box and click OK to open Registry Editor-> find out all registry entries above and delete them
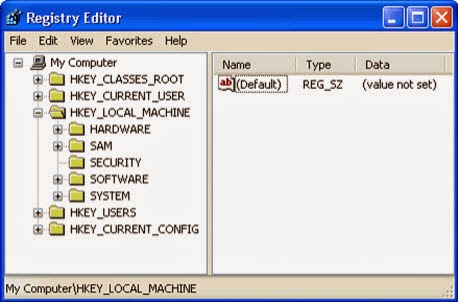
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Settings
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Associations "LowRiskFileTypes"=".zip;.rar;.nfo;.txt;.exe;.bat;.com;.cmd;.reg;.msi;.htm;.html;.gif;.bmp;.jpg;.avi;.mpg;.mpeg;.mov;.mp3;.m3u;.wav;"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Attachments "SaveZoneInformation"=1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msseces.exe "Debugger"="svchost.exe"
Method 2: Automatic Removal with SpyHunter
SpyHunter is a world-famous real-time malware protection and removal tool, which is designed to detect , remove and protect your PC from the latest malware attacks, such as Trojans, worms, rootkits, rogue viruses, browser hijacker, ransomware, adware, key-loggers, and so forth. To keep SpyHunter Anti-malware on your computer is an important way to protect your computer in a good condition. Please find the instruction as follow.
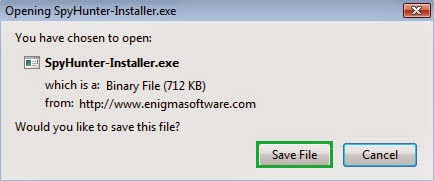
Step 1: Press the following button to download SpyHunter.
Step 2: Save the file onto your computer and click on the Run button to install it.
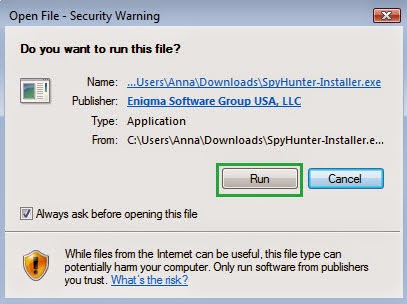
Step 3: After finishing the installation processes, scan your computer to find out potential threats.


6158)AZRTJ6S.jpg)
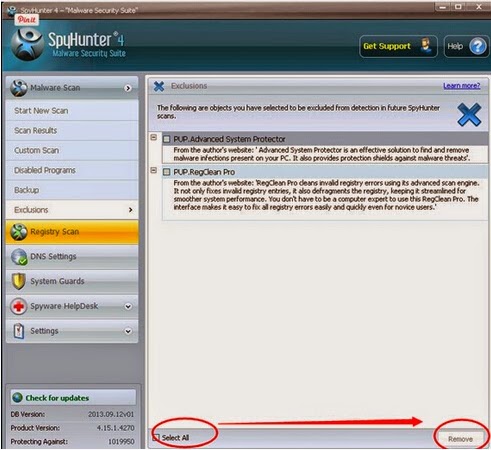
Step 4: Tick Select all and then Remove to delete all threats.
Guide to download RegCure Pro to optimize PC
If you are still worried about the left over of CTB-Locker(Critoni) and want to clean all the unwanted registry entries, it is recommended to use RegCure Pro.
Step 1. Install and launch RegCure Pro on your PC.
Step 2. Select "Yes" to download and install RegCure Pro.

Step 3. Click "Next" to continue.

Step 4. RegCure Pro will open automatically on your screen.

Step 5. RegCure Pro is scanning your PC for error.

Step 6. After scanning, choose the issues you want to fix.


Step 3. Click "Next" to continue.



Step 6. After scanning, choose the issues you want to fix.




No comments:
Post a Comment