Exploit:Java/CVE-2013-2465 is a risky computer threats which will leave you a unstable and sluggish computer system. Your sensitive information like credit card or passwords will be sent to the third parties to make profits. You are not able to get access to the programs or other items you want to use. That is to say, your PC is of no use, you are not able to use it any more.
Some features of Exploit:Java/CVE-2013-2465
It can make modifications of your browser and system settings.
Your whole computer system will be flooded with a lot of junk files or other computer threats.
Your PC will be turned to be sluggish and you are not able to get access to the Internet.
Your sensitive information will be collected.
Exploit:Java/CVE-2013-2465 Removal Guide
Guide 1: To manually delete all its related items like the steps showed below
<Restart your computer. As your computer restarts but before Windows launches, tap "F8" key constantly. Use the arrow keys to highlight the "Safe Mode with Networking" option, and then press ENTER>
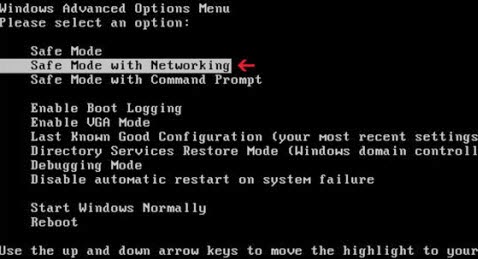
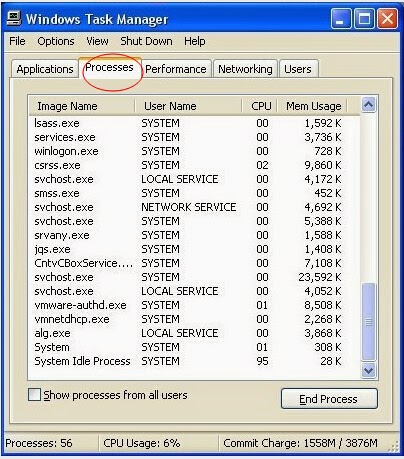
b: Stop all the related processes of Exploit:Java/CVE-2013-2465
Press Ctrl+Alt+Del together to open Task Manager -> click on processes and tick Processes from all users box -> click on End Process to end all processes

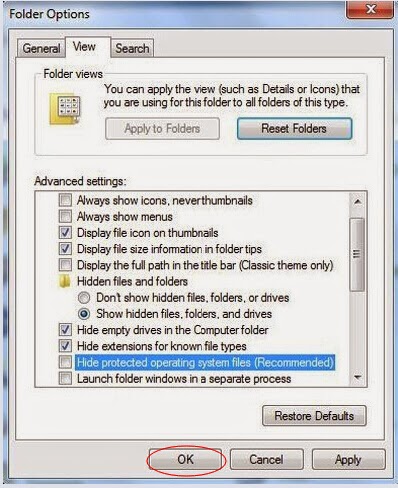
When Folder Options window opens, click on its View tab, tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then press OK.
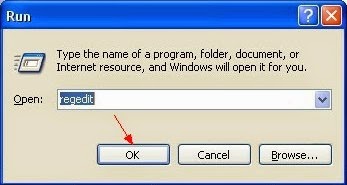
d: Delete all the related registry entries
Press Windows+R to launch Run…-> type Regedit into Open box and click OK to open Registry Editor-> find out all registry entries above and delete them
Press Windows+R to launch Run…-> type Regedit into Open box and click OK to open Registry Editor-> find out all registry entries above and delete them
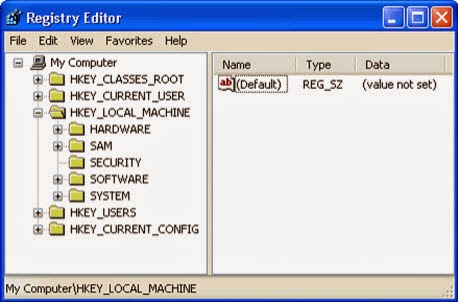
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Exploit:Java/CVE-2013-2465 " = "%AppData%\<random>.exe"
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run "Exploit:Java/CVE-2013-2465 " = "%AppData%\<random>.exe"
e: Remove infected files
%AppData%\<random>.exe
%CommonAppData%\<random>.exe
C:\Windows\Temp\<random>.exe
%temp%\<random>.exe
C:\Program Files\<random>
e: Remove infected files
%AppData%\<random>.exe
%CommonAppData%\<random>.exe
C:\Windows\Temp\<random>.exe
%temp%\<random>.exe
C:\Program Files\<random>
Guide 2: To safely and automatically uninstall it with SpyHunter
SpyHunter is a world-famous real-time malware protection and removal tool, which is designed to detect , remove and protect your PC from the latest malware attacks, such as Trojans, worms, rootkits, rogue viruses, browser hijacker, ransomware, adware, key-loggers, and so forth. To keep SpyHunter Anti-malware on your computer is an important way to protect your computer in a good condition. Please find the instruction as follow.Step 1: Click the icon to download SpyHunter.
Step 2: Click to Run the file.
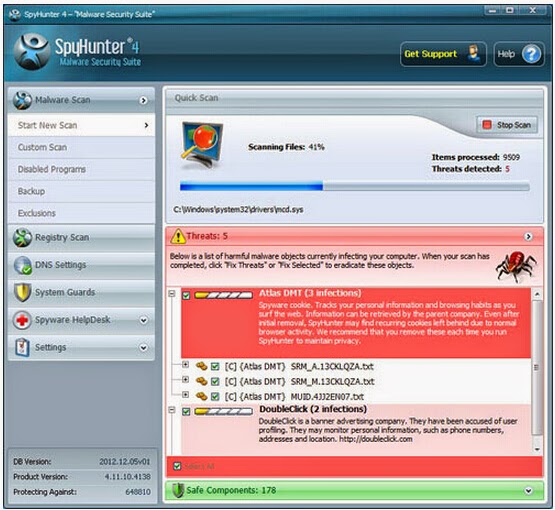
Step 3: After installation, click Start New Scan to find out potential threats.
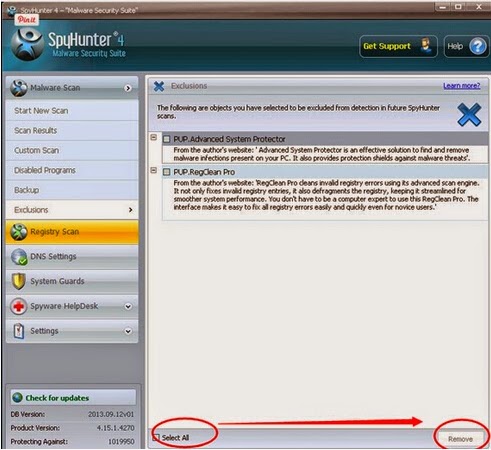
Step 4: Select All and Remove all reported threat.
Guide to download RegCure Pro to optimize PC
If you are still worried about the left over of Exploit:Java/CVE-2013-2465 and want to clean all the unwanted registry entries, it is recommended to use RegCure Pro. RegCure Pro is packed with the tools you need to boost your PC’s speed and performance. Featuring an intuitive interface and easy-to-use work flow, RegCure Pro scans common problem areas – and quickly and safely fixes them. As well, it has several tools and features to address other performance and computing issues.
Step 1. Install and launch RegCure Pro on your PC.
Step 2. Click "Yes" to download and install RegCure Pro.

Step 3. Click "Next" to continue.

Step 4. RegCure Pro will open automatically on your screen.

Step 5. RegCure Pro is scanning your PC for error.

Step 6. After scanning, choose the issues you want to fix.





Step 6. After scanning, choose the issues you want to fix.

Conclution: Manual removal Exploit:Java/CVE-2013-2465 is a very complex and difficult process. If you don’t have sufficient expertise in dealing with the manual removal, Install Spyhunter can be your better choice. It is capable of auto-detecting and removing viruses. You can also Download RegCure Pro to help you remove unneeded registry files and optimize the computer.



No comments:
Post a Comment