CryptoTorLocker2015 Ransomware Description
CryptoTorLocker2015 is a new ransomware virus that could attack computer from all over the world. Once executed, it will change the computer registry entries and system files and then begin to encrypt your files, including photos, videos, documents, usb disk, etc. You will get a message just like the picture shows as below.
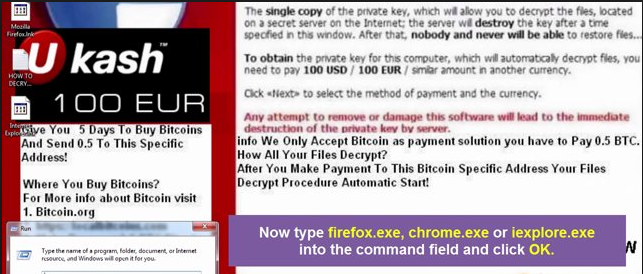
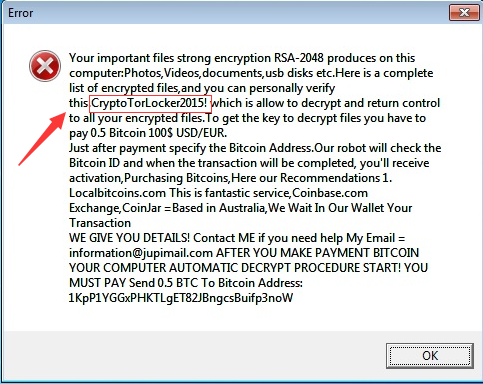
It uses unique bitcoin payment addresses for each victim instead of hard coded links. It states that you need to pay 0.5 BTC to decrypt the files. If you are one of the unfortunate victims, don’t pay the money. There is no guarantee that you can get your files back. What you should do is to remove the virus completely to avoid more files from being encrypted.
How to decrypt your files?
How can CryptoTorLocker2015 get into the computer?
1. Malware authors often use tricks to try to convince you to download malicious files from the spam email attachment.
2. Many viruses spread by infecting removable drives such as USB flash drives or external hard drives.
3. Some malware can be installed at the same time as other programs that you download.
4. Some programs will also install other applications that we detect as potentially unwanted software.
5. Malware can use hacked or compromised webpage to spread virus.
6. Some types of malware can download other threats to your PC.
Guide for Removing CryptoTorLocker2015
Restart your computer. As your computer restarts but before Windows launches, tap “F8″ key constantly. Use the arrow keys to highlight the “Safe Mode with Networking” option, and then press ENTER

Step two: Pressing keys “CTRL + Shift + ESC” to open the Task Manager, and then end all CryptoTorLocker2015 running processes.
![windows-task-manager-processes[1]](http://blog.teesupport.com/wp-content/uploads/2012/07/windows-task-manager-processes118.png)
random.exe
Step three: Click on the “Start” menu and then click on the “Search programs and files” box to clear up all files created by CryptoTorLocker2015:
%AppData%\NPSWF32.dll %AppData%\random.exe %AppData%\result.dbStep four: Open Registry Editor by navigating to “Start” Menu, type “Regedit” into the box and click “OK” to proceed. When Registry Editor is open, remove all related registry entries to CryptoTorLocker2015:


HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Inspector %AppData%\random.exe HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\WarnOnHTTPSToHTTPRedirect 0 HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\ID 4 HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\UID [rnd] HKCU\Software\Microsoft\Windows\CurrentVersion\Settings\net [date of installation] HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorAdmin 0 HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\ConsentPromptBehaviorUser 0 HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system\EnableLUA 0 HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AAWTray.exe\Debugger svchost.exe HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVCare.exe\Debugger svchost.exe HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVENGINE.EXE\Debugger svchost.exe
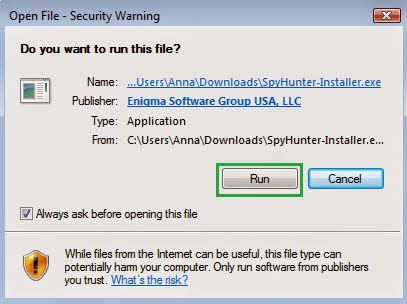
Step five: Deleting CryptoTorLocker2015 by installing Anti-Malware program SpyHunter
1) Click the icon below to download Spyhunter.

2) Install Spyhunter step by step:
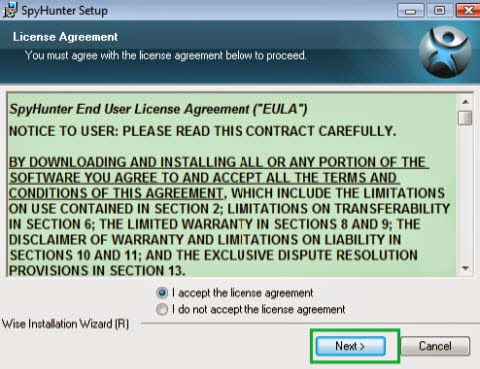
3) Start a full and quick scan with SpyHunter .
.jpg)
4) Remove detected threats.
Attention
CryptoTorLocker2015 is a quite harmful Trojan horse. The sooner you take actions, the less danger your computer will face. Thus, you should get CryptoTorLocker2015 out of your computer immediately once you find out its trace. Here I strongly recommend you to use the automatic way to remove CryptoTorLocker2015. Therefore, downloading Anti-Malware program SpyHunter is your best choice. For it is safe, reliable and convenient. It can help you to delete virus thoroughly and can prevent your computer from attacking in the future.

No comments:
Post a Comment