Here in this post, there will be some useful tips on hoe to remove Rerdom_CriminalFinancial_Asprox, hope it can help.
Brief Introduction about Rerdom_CriminalFinancial_Asprox
Similar to Multi_CriminalClick-ClickThrough, Rerdom_CriminalFinancial_Asprox is also a kind of bot virus. What is a bot? Bots are one of the most sophisticated types of crimeware facing the Internet today. Bots are similar to worms and Trojans, but earn their unique name by performing a wide variety of automated tasks on behalf of their master (the cybercriminals) who are often safely located somewhere far across the Internet. Tasks that bots can perform run the gamut from sending spam to blasting Web sites off the Internet as part of a coordinated "denial-of-service" attack. Since a bot infected computer does the bidding of its master, many people refer to these victim machines as "zombies."
Bots sneak onto a person's computer in many ways. Bots oftentimes spread themselves across the Internet by searching for vulnerable, unprotected computers to infect. When they find an exposed computer, they quickly infect the machine and then report back to their master. Their goal is then to stay hidden until they are awoken by their master to perform a task. Bots do not work alone, but are part of a network of infected machines called a "botnet." Botnets are created by attackers repeatedly infecting victim computers using one or several of the techniques mentioned above. The cyber criminals can use this bots to do many malicious activities on your computer. With this virus, they are able to get into the computer to steal your personal information. This is a dangerous virus which should be removed immediately. And it is highly recommended to keep a powerful anti-virus like Spyhunter on the computer to remove and block viruses.
Similar to Multi_CriminalClick-ClickThrough, Rerdom_CriminalFinancial_Asprox is also a kind of bot virus. What is a bot? Bots are one of the most sophisticated types of crimeware facing the Internet today. Bots are similar to worms and Trojans, but earn their unique name by performing a wide variety of automated tasks on behalf of their master (the cybercriminals) who are often safely located somewhere far across the Internet. Tasks that bots can perform run the gamut from sending spam to blasting Web sites off the Internet as part of a coordinated "denial-of-service" attack. Since a bot infected computer does the bidding of its master, many people refer to these victim machines as "zombies."
Bots sneak onto a person's computer in many ways. Bots oftentimes spread themselves across the Internet by searching for vulnerable, unprotected computers to infect. When they find an exposed computer, they quickly infect the machine and then report back to their master. Their goal is then to stay hidden until they are awoken by their master to perform a task. Bots do not work alone, but are part of a network of infected machines called a "botnet." Botnets are created by attackers repeatedly infecting victim computers using one or several of the techniques mentioned above. The cyber criminals can use this bots to do many malicious activities on your computer. With this virus, they are able to get into the computer to steal your personal information. This is a dangerous virus which should be removed immediately. And it is highly recommended to keep a powerful anti-virus like Spyhunter on the computer to remove and block viruses.
Bots sneak onto a person's computer in many ways. Bots oftentimes spread themselves across the Internet by searching for vulnerable, unprotected computers to infect. When they find an exposed computer, they quickly infect the machine and then report back to their master. Their goal is then to stay hidden until they are awoken by their master to perform a task. Bots do not work alone, but are part of a network of infected machines called a "botnet." Botnets are created by attackers repeatedly infecting victim computers using one or several of the techniques mentioned above. The cyber criminals can use this bots to do many malicious activities on your computer. With this virus, they are able to get into the computer to steal your personal information. This is a dangerous virus which should be removed immediately. And it is highly recommended to keep a powerful anti-virus like Spyhunter on the computer to remove and block viruses.
How to prevent from being infected by Rerdom_CriminalFinancial_Asprox ?
1. Never click on a link or attachment in an email that you are not positive is from a trusted source;
2. Beware of internet pop-ups;
3. Set up your Windows Update to automatically download patches and upgrades;
4. Be wary of files with a double extension such as .txt.vb or .jpg.exe.
5. Install real-time anti-spyware protection and Keep anti-malware applications current.
6. Don’t get access to illegal online contents such as gambling or porn.
1. Never click on a link or attachment in an email that you are not positive is from a trusted source;
2. Beware of internet pop-ups;
3. Set up your Windows Update to automatically download patches and upgrades;
4. Be wary of files with a double extension such as .txt.vb or .jpg.exe.
5. Install real-time anti-spyware protection and Keep anti-malware applications current.
6. Don’t get access to illegal online contents such as gambling or porn.
2. Beware of internet pop-ups;
3. Set up your Windows Update to automatically download patches and upgrades;
4. Be wary of files with a double extension such as .txt.vb or .jpg.exe.
5. Install real-time anti-spyware protection and Keep anti-malware applications current.
6. Don’t get access to illegal online contents such as gambling or porn.
Removal Guide for Rerdom_CriminalFinancial_Asprox
Guide 1: To manually delete all its related items like the steps showed below
Step 1: Restart computer in safe mode.
Keep pressing F8 key before Windows interface launches. When Windows Advanced Options menu turns up, select Safe Mode with Networking and tap Enter key.
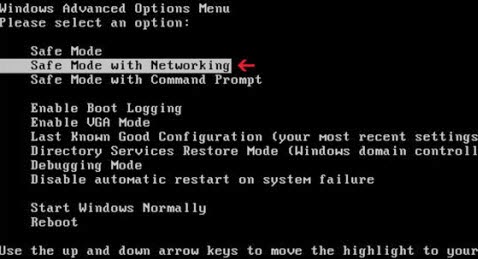
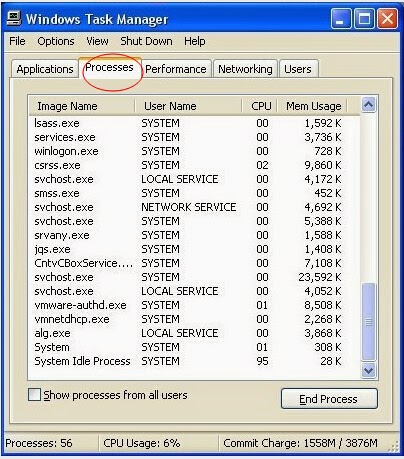
Step 2: End all running process in Task Manager

Press Ctrl+Alt+Del together to open Task Manager -> click on processes and tick Processes from all users box -> click on End Process to end all processes

Step 3: Delete the Trojan program from Uninstall a program in Control Panel
Open Start menu and choose Control Panel -> select Uninstall a program -> choose the Trojan program and right click the Uninstall button on your right to delete it
Step 4: Open Control Panel from Start menu and search for Folder Options.
When Folder Options window opens, click on its View tab, tick Show hidden files and folders and non-tick Hide protected operating system files (Recommended) and then press OK.
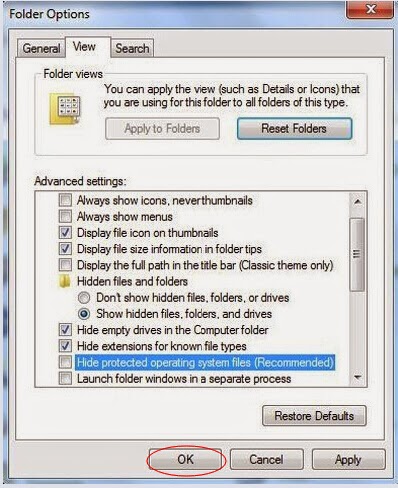
Step 5: Remove all entries below in Registry Editor:
Press Windows+R to launch Run…-> type Regedit into Open box and click OK to open Registry Editor-> find out all registry entries above and delete them
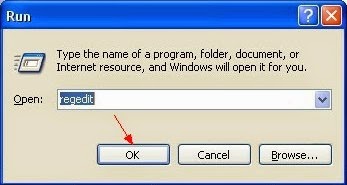
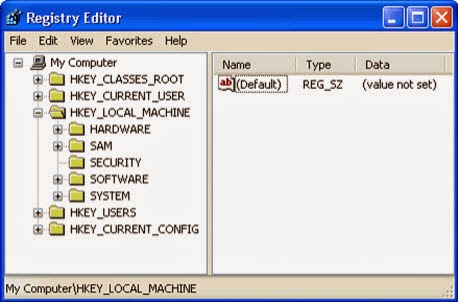
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Multi_CriminalClick-ClickThrough " = "%AppData%\<random>.exe"
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run "Multi_CriminalClick-ClickThrough " = "%AppData%\<random>.exe"
Guide 2: To safely and automatically uninstall it with SpyHunter
SpyHunter is a real-time and effective antivirus. Though you have had a safeguard before, it can still be installed as an assistant one. Then, your computer will have double security.Step 1: Press the following icon to download SpyHunter.
Step 2: Get it saved in your computer and click the Run choice to install it step by step.
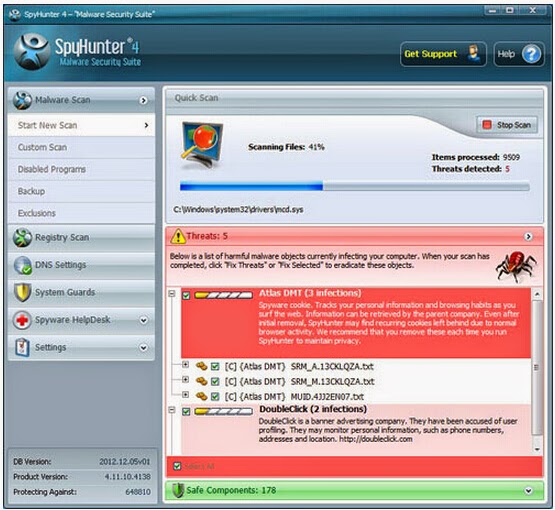
Step 4:Tick Select All and then Remove to delete all reported threat.
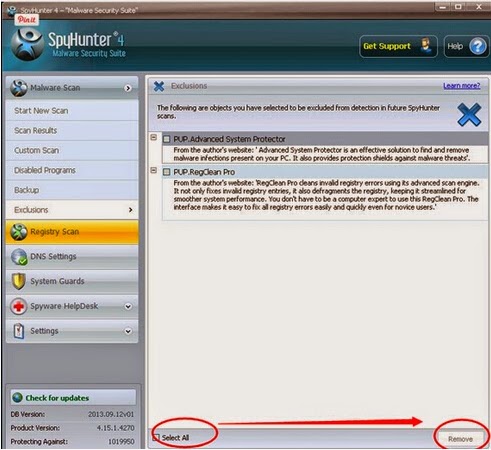
If you are still worried about the left over of Rerdom_CriminalFinancial_Asprox and want to clean all the unwanted registry entries, or want to uninstall other specific programs, it is recommended to use Perfect Uninstaller.
Guide to download RegCure Pro to optimize PC
If you are still worried about the left over of Rerdom_CriminalFinancial_Asprox and want to clean all the unwanted registry entries, it is recommended to use RegCure Pro.
Step 1. Install and launch RegCure Pro on your PC.
Step 2. Select "Yes" to download and install RegCure Pro.

Step 3. Click "Next" to continue.

Step 4. RegCure Pro will open automatically on your screen.

Step 5. RegCure Pro is scanning your PC for error.

Step 6. After scanning, choose the issues you want to fix.





Step 6. After scanning, choose the issues you want to fix.

Conclusion: Bots can be very destructive. It compromises your computer and also your privacy. Please don’t wait until it has caused unalterable damages. Manual removal is complex and risky task, as it refers to key parts of computer system, and is recommended only for advanced users. Download SpyHunter to block and remove it automatically and safely now. You can also Download RegCure Pro to help you clean up unwanted registry entries and files so as to optimize the computer.




No comments:
Post a Comment