Overview of Home.sweetim.com
Type: Redirect Virus
Alert level: Severe
Targeted Browsers:Internet Explorer, Firefox, Google Chrome, and so on.
Targeted OS: Windows XP, Windows Vista, Windows 7
Home.sweetim.com is a malicious browser hijacker that are attacking random computer users all over the world. It is installed on targeted computers out of permission and notification. When Home.sweetim.com lurks into the system successfully, it will arouse great damage and make lots of changes to the compromised computer. What are they? What is more, maybe you have the latest protection tools, but they just can’t do auto removal for you. Then you need to follow manual removal steps, don’t know how? More details about Home.sweetim.com will be listed as followings.
Home.sweetim.com Screen Screenshot

Home.sweetim.com is Really Hazardous
* Home.sweetim.com will change the homepage to be its own one.
* Home.sweetim.com will constantly redirect your internet connection and tell you that you are browsing unsafely.
* Home.sweetim.com may insert an add-on or plug-in to the web browser to arouse irritating pop ups when you are surfing the Internet.
*Home.sweetim.com may bring or invite rogue programs, malware, Trojan, and so on.
*Home.sweetim.com can monitor your online habits.
*Home.sweetim.com will slow down system performance significantly.
* Home.sweetim.com may help cyber hackers to capture personal information stored on the computer.
How to Delete Home.sweetim.com?
Method 1: Getting rid of Home.sweetim.com manually
[random name].exe of Home.sweetim.comStep 2: Detect and delete all registry entries:
HKEY_LOCAL_MACHINESOFTWAREClassesCLSID[random] HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuardCurVer HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuardCLSID HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuard HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuard.1 HKEY_LOCAL_MACHINESOFTWAREMicrosoftInternet ExplorerToolbar “[trojan name] Toolbar”
%System%drivers[RANDOM CHARACTERS].sys %AppData%[trojan name]toolbarcouponscategories.xml %AppData%[trojan name]toolbarcouponsmerchants.xml %AppData%[trojan name]toolbarcouponsmerchants2.xml %AppData%[trojan name]toolbardtx.ini %AppData%[trojan name]toolbarguid.dat %AppData%[trojan name]toolbarlog.txt %AppData%[trojan name]toolbarpreferences.dat %AppData%[trojan name]toolbarstat.log %AppData%[trojan name]toolbarstats.dat %AppData%[trojan name]toolbaruninstallIE.dat %AppData%[trojan name]toolbaruninstallStatIE.dat %AppData%[trojan name]toolbarversion.xml %Temp%[trojan name]toolbar-manifest.xml
Method 2: Getting rid of Home.sweetim.com automatically
3) Execute a full scan with SpyHunter and remove all detected threats.
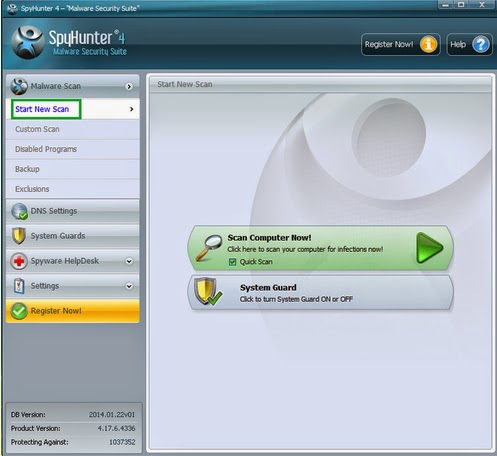
4) Remove associated programs.
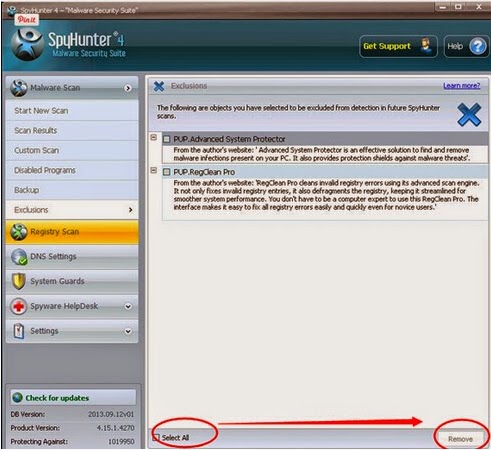
Note
You may meet with lots of difficulties even make the issue worse than before if you don't have sufficient manual removal skills. To ensure that you can remove Home.sweetim.com completely and safely, you are advised to install Anti-Malware program SpyHunter. It is easy, efficient and automatic. What’s more, it won’t damage your computer. It serves not only a role of removing the malware program, but also a role of protecting your computer from threats in the future.

No comments:
Post a Comment