Let’s Know More About 22Apple.com
At the same time, 22Apple.com can spread with high speed. And it is capable of changing from time to time with random names. That is why your antivirus program can’t catch 22Apple.com even it is the latest version. Maybe some of your antivirus program works, but you can’t do full scan for tens of hundreds of detections created by 22Apple.com, which will result in slow system performance.
In order to remove such redirect virus, you need to find all its rooted files associated with program files, processes, dll files and registry entries. Have no experience of removing the virus? Is there any one can walk you through? You can follow detailed removal instructions in this post.
How 22Apple.com Can Get Into The Sytem?

Normally, many computer users find 22Apple.com on the computer, but just can’t recall when they got the virus for it secretly enters to the system out of permission and awareness. This redirect virus can be brought with another Trojan infection. Rootkit and Zeroaccess Trojan are the main vectors to bundle with 22Apple.com. For many websites with badly reputation offer computer threat like Trojan, adware, malware, and so on. Hence, you should be careful when you surf the Internet or you may install the virus with carelessness. On the other way, sharing files with others can be risky to get this virus. Last but not least, opening email attachments is another access for 22Apple.com virus.
Harmful Properties of 22Apple.com
- 22Apple.com lurks into the system out of your permission and notification.
- 22Apple.com can be infected with many ways.
- Hijack your web browser, change the homepage, redirect web searches.
- When you want to search for something, 22Apple.com pops up.
- It may communicate with remote hackers to steal your private information.
- 22Apple.com may invite other computer threats.
- 22Apple.com will slow down system performance
Precautions
(2) Avoid opening unknown e-mail attachments.
(3) Don’t click unknown links or pop ups.
(4) Be careful when you want to download some free resources from Internet.
(5) Be cautious when you want to share files with others.
Removal Instructions of 22Apple.com
Step 1: Disable Proxy:
- For Firefox: Clik the “Firefox” button in the upper left of Firefox browser menu and then hit “Options" ; Select the "Advanced" tab; Click the “network”tab and then the “settings”button on the ''Option window; Checkmark option“No Proxy”; Click “OK” and then “OK” again to disable proxy settings.
- For Google Chrome: Open Google Chrome ; Go to the key at the top right, then “Options”->”Advanced”; Click “Change proxy settings” located in “Network”; Click “Connections” tab; Click “LAN Settings”; Checkmark “Do not activate a proxy server”.
- For Internet Explorer: Open Internet Explorer; Click Tools; Click on Internet Options; In the Internet Options window click "Connections tab", Then click on the LAN settings button" Uncheck the check box labeled “Use a proxy server for your LAN” under the Proxy Server section and press "OK".
Step 2:Press Ctrl+Alt+Del keys together to run the Windows Task Manager, and stop all 22Apple.com processes

Step 3: Delete all of the related registry entries of 22Apple.com.

(Click Start button> click "Run" > Input "regedit" into the Run box and click ok)
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\{random}
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\DisallowRun
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Regedit32
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Current\Winlogon\”Shell” = “{random}.exe”
Step 4: Delete 22Apple.com by installing SpyHunter

2) Install Spyhunter Step by Step:
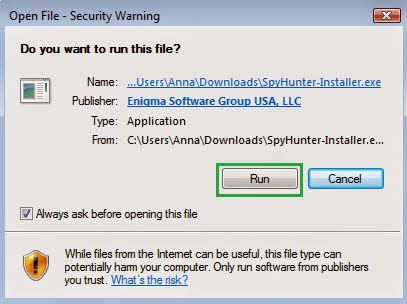
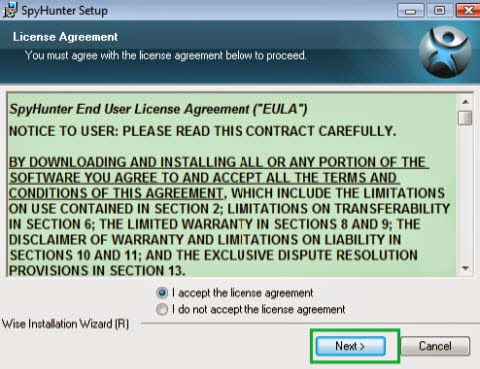
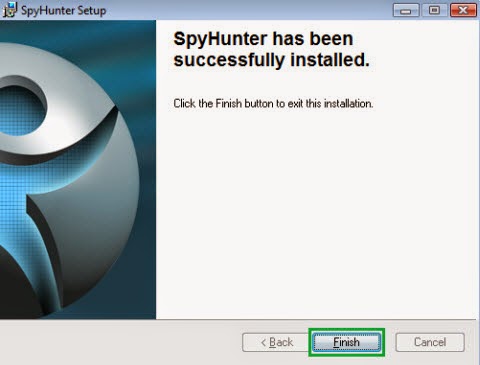
3) Start a full and quick scan with SpyHunter .
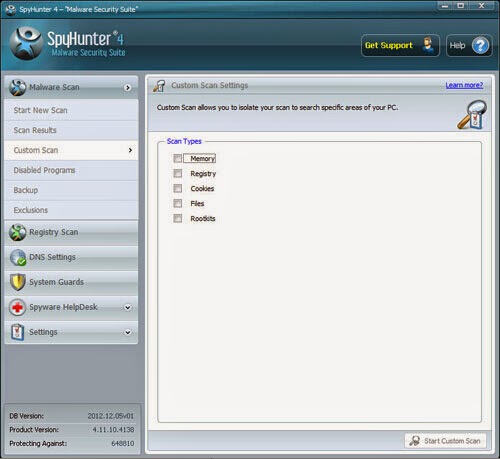.jpg)
4) Remove detected threats.
Advice
If you not a computer expert, you resort to the automatic way. For a layman, manually to remove 22Apple.com is not so easy to master. Thus, there is no need for you to use this way. On the contrary, you’d better install Anti-Malware program SpyHunter to help you to remove 22Apple.com. On one hand, it can work effectively; on the other hand, it can protect your computer from infecting in the future.

No comments:
Post a Comment